- Joined
- April 6, 2025
- Messages
- 291
- Reaction score
- 2,907
- Points
- 93
- Thread Author
- #1
Putting the wireless card into monitor mode
To search for networks with WPS, as well as to attack them, we need to switch the WiFi card to monitor mode.
We close tools that can prevent our attack:
Find out the name of the wireless interface:
WiFi WPS Attack using Reaver
What is WPS?
WiFi Protected Setup (secure installation), WPS – standard (and the same protocol) of the semi-automatic creation of a wireless WiFi network.
WPS was designed to simplify deployment and connect to WiFi networks.
There are two types of WPS: WPS with a pin code of 8 digits, on the client you need to enter the same code as on the access point, and the WPS button – you need to press a button on the access point and on the client with an interval of less than two minutes, then they will connect together.
Access points that have WPS enabled are vulnerable to a brute-force (brute-force) attack of this PIN. Once the WPS PIN is selected, you can connect to the access point, as well as learn its WPA / WPA2 password. The search is possible only on access points for which you need to enter numbers, but it is not possible where you need to press buttons.
All you need to go through only 11,000, which can be done in hours-days.
Different tools are used for sorting WPS PINs, the most popular are Reaver and Bully. In this manual, I’ll show you how to use Reaver to hack WiFi.
WPS vulnerability
In December 2011, Stefan Fibök (born Stefan Viehböck) and Craig Heffner (born Craig Heffner) talked about serious flaws in the WPS protocol. It turned out that if WPS with PIN is activated on the access point (which is enabled by default on most routers), then you can pick up the PIN for connection in a matter of hours.
The PIN code consists of eight digits — hence, there are 108 (100,000,000) PIN variants for selection. However, the number of options can be significantly reduced. The fact is that the last digit of the PIN is a checksum that can be calculated from the first seven digits. Thus, the number of options is already reduced to 107 (10 000 000).
WPS authorization involves the client sending a sequence of PIN numbers and M4 or M6 packets and replies to them from the base station. If the first 4 digits of the PIN-code are incorrect, then having received their access point will send the EAP-NACK immediately after receiving the M4, and if there was an error in the last 3 digits of the right-hand side (we don’t consider the 8th because it is easily generated by the attacker using the formula) after receiving M6. Thus, the lack of a protocol allows you to divide the PIN into two parts, 4 initial digits and 3 subsequent ones and check each part for correctness using the base station as an oracle, which tells you whether the correct sequence of digits has been sent.
If the PIN-code is divided into two parts: Consequently, it turns out 10 4 (10 000) options for the first half and 10 3 (1000) for the second. As a result, this amounts to only 11,000 variants for complete enumeration, which is more than 9000 times less than the initial number of variants 10 8 .
Thus, instead of one large space of values of 10 7, we get two of 10 4 and 10 3 , and, of course, 10 7 <> 10 4 +10 3 . As a result, it suffices to test 11,000 combinations (more than 4 digits per thousand) instead of 10,000,000.
Vulnerabilities were also discovered in the random number generator of some manufacturers’ routers. Vulnerability called pixie dust . For vulnerable routers, you can get a pin after the first attempt and offline brutfors.
WPS Anti-Burglary Protection
It is possible to defend against an attack in one way so far – disable WPS with a pin in the settings of the router. However, it is not always possible to do this, sometimes WPS is disabled only completely. The most that manufacturers can do is to release a firmware that allows you to enter a timeout for blocking a function, for example, after 5 unsuccessful attempts to enter a PIN code, which will complicate the brute force and increase the time for an attacker to pick up the identifier.
Which wireless card is suitable for iterating over WPS
A wireless card is needed that supports monitor mode and is capable of giving injections. Those. in theory, any map from this list should have come up .
But in practice, there are several bugs in Reaver, which make it impossible to iterate over WPS pins using wireless cards with a Ralink chipset that use rt2800usb drivers (RT3070, RT3272, RT3570, RT3572 chips, etc.), as well as for cards with a chipset Intel
Reaver developers (reaver-wps-fork-t6x mod) are trying to correct this situation, several bugs have already been fixed in the latest release, but the work has not yet been completed. At the time of writing, it is recommended to use the Alfa AWUS036NHA wireless adapter with Reaver, since it has an Atheros AR9271 chipset that works great with Reaver.
WPS Attack Algorithm
To search for networks with WPS, as well as to attack them, we need to switch the WiFi card to monitor mode.
We close tools that can prevent our attack:
Find out the name of the wireless interface:
And put it into monitor mode (replace wlan0 with the name of your interface, if it is different):
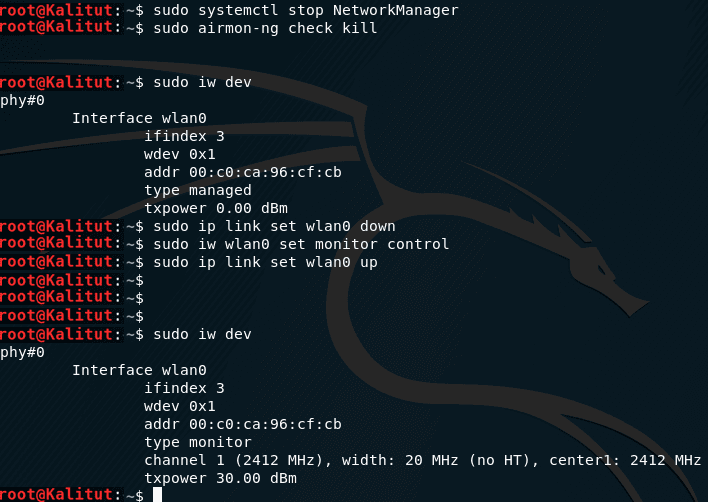
The new network interface in monitor mode is also called wlan0 .
If you have a different name for the wireless network interface, then in all subsequent commands, insert it instead of wlan0 .
Search for access points with WPS enabled
Very many APs have WPS functionality. But for many, this feature is disabled, and for those with it enabled, it can be blocked (for example, due to several unsuccessful attempts to pick up a PIN).
To collect information about access points, we will use the tool Wash , which comes with Reaver, and it is for this purpose intended.
And put it into monitor mode (replace wlan0 with the name of your interface, if it is different):
To search for networks with WPS, as well as to attack them, we need to switch the WiFi card to monitor mode.
We close tools that can prevent our attack:
| sudo systemctl stop NetworkManager sudo airmon-ng check kill |
WiFi WPS Attack using Reaver
May 27, 2019 by Walid SalameWiFi WPS Attack using Reaver
What is WPS?
WiFi Protected Setup (secure installation), WPS – standard (and the same protocol) of the semi-automatic creation of a wireless WiFi network.
WPS was designed to simplify deployment and connect to WiFi networks.
There are two types of WPS: WPS with a pin code of 8 digits, on the client you need to enter the same code as on the access point, and the WPS button – you need to press a button on the access point and on the client with an interval of less than two minutes, then they will connect together.
Access points that have WPS enabled are vulnerable to a brute-force (brute-force) attack of this PIN. Once the WPS PIN is selected, you can connect to the access point, as well as learn its WPA / WPA2 password. The search is possible only on access points for which you need to enter numbers, but it is not possible where you need to press buttons.
All you need to go through only 11,000, which can be done in hours-days.
Different tools are used for sorting WPS PINs, the most popular are Reaver and Bully. In this manual, I’ll show you how to use Reaver to hack WiFi.
WPS vulnerability
In December 2011, Stefan Fibök (born Stefan Viehböck) and Craig Heffner (born Craig Heffner) talked about serious flaws in the WPS protocol. It turned out that if WPS with PIN is activated on the access point (which is enabled by default on most routers), then you can pick up the PIN for connection in a matter of hours.
The PIN code consists of eight digits — hence, there are 108 (100,000,000) PIN variants for selection. However, the number of options can be significantly reduced. The fact is that the last digit of the PIN is a checksum that can be calculated from the first seven digits. Thus, the number of options is already reduced to 107 (10 000 000).
WPS authorization involves the client sending a sequence of PIN numbers and M4 or M6 packets and replies to them from the base station. If the first 4 digits of the PIN-code are incorrect, then having received their access point will send the EAP-NACK immediately after receiving the M4, and if there was an error in the last 3 digits of the right-hand side (we don’t consider the 8th because it is easily generated by the attacker using the formula) after receiving M6. Thus, the lack of a protocol allows you to divide the PIN into two parts, 4 initial digits and 3 subsequent ones and check each part for correctness using the base station as an oracle, which tells you whether the correct sequence of digits has been sent.
If the PIN-code is divided into two parts: Consequently, it turns out 10 4 (10 000) options for the first half and 10 3 (1000) for the second. As a result, this amounts to only 11,000 variants for complete enumeration, which is more than 9000 times less than the initial number of variants 10 8 .
Thus, instead of one large space of values of 10 7, we get two of 10 4 and 10 3 , and, of course, 10 7 <> 10 4 +10 3 . As a result, it suffices to test 11,000 combinations (more than 4 digits per thousand) instead of 10,000,000.
Vulnerabilities were also discovered in the random number generator of some manufacturers’ routers. Vulnerability called pixie dust . For vulnerable routers, you can get a pin after the first attempt and offline brutfors.
WPS Anti-Burglary Protection
It is possible to defend against an attack in one way so far – disable WPS with a pin in the settings of the router. However, it is not always possible to do this, sometimes WPS is disabled only completely. The most that manufacturers can do is to release a firmware that allows you to enter a timeout for blocking a function, for example, after 5 unsuccessful attempts to enter a PIN code, which will complicate the brute force and increase the time for an attacker to pick up the identifier.
Which wireless card is suitable for iterating over WPS
A wireless card is needed that supports monitor mode and is capable of giving injections. Those. in theory, any map from this list should have come up .
But in practice, there are several bugs in Reaver, which make it impossible to iterate over WPS pins using wireless cards with a Ralink chipset that use rt2800usb drivers (RT3070, RT3272, RT3570, RT3572 chips, etc.), as well as for cards with a chipset Intel
Reaver developers (reaver-wps-fork-t6x mod) are trying to correct this situation, several bugs have already been fixed in the latest release, but the work has not yet been completed. At the time of writing, it is recommended to use the Alfa AWUS036NHA wireless adapter with Reaver, since it has an Atheros AR9271 chipset that works great with Reaver.
WPS Attack Algorithm
- Putting the wireless interface in monitor mode
- Looking for targets to attack
- Check for exposure to Pixie Dust
- We are trying to find out if PINs come from a database of known PINs and are generated by certain algorithms.
- We run a full brute force if the previous steps failed.
- If you received a PIN, but the WPA password is not shown, then run the commands to get the password from WiFi.
To search for networks with WPS, as well as to attack them, we need to switch the WiFi card to monitor mode.
We close tools that can prevent our attack:
| sudo systemctl stop NetworkManager sudo airmon-ng check kill |
| sudo iw dev |
| sudo ip link set wlan0 down sudo iw wlan0 set monitor control sudo ip link set wlan0 up |

The new network interface in monitor mode is also called wlan0 .
If you have a different name for the wireless network interface, then in all subsequent commands, insert it instead of wlan0 .
Search for access points with WPS enabled
Very many APs have WPS functionality. But for many, this feature is disabled, and for those with it enabled, it can be blocked (for example, due to several unsuccessful attempts to pick up a PIN).
To collect information about access points, we will use the tool Wash , which comes with Reaver, and it is for this purpose intended.
| sudo wash -i wlan0 |
| sudo iw dev |
| sudo ip link set wlan0 down sudo iw wlan0 set monitor control sudo ip link set wlan0 up The new network interface in monitor mode is also called wlan0 . If you have a different name for the wireless network interface, then in all subsequent commands, insert it instead of wlan0 . Search for access points with WPS enabled Very many APs have WPS functionality. But for many, this feature is disabled, and for those with it enabled, it can be blocked (for example, due to several unsuccessful attempts to pick up a PIN). To collect information about access points, we will use the tool Wash , which comes with Reaver, and it is for this purpose intended.
|


