- Joined
- April 6, 2025
- Messages
- 291
- Reaction score
- 3,104
- Points
- 93
- Thread Author
- #1
Anonym8 is a free and open-source tool for becoming anonymous on the Internet while testing the security of a web browser. Anonym8 uses IP-tables to create a Transparent Proxy through the Tor Network. Anonym8 can move the network of your Kali Linux operating system through the Tor Network. When you run the tool, it starts as a transparent proxy. After initiating Anonym8, you can do all your security testing on the website and become anonymous. This tool can be challenging for people if they want to trace your IP address. This tool uses the techniques of Transparent Proxy through TOR and I2P to change Mac addresses. The user interface is very similar to Metasploitable 1 and Metasploitable 2, which makes it easy to use.
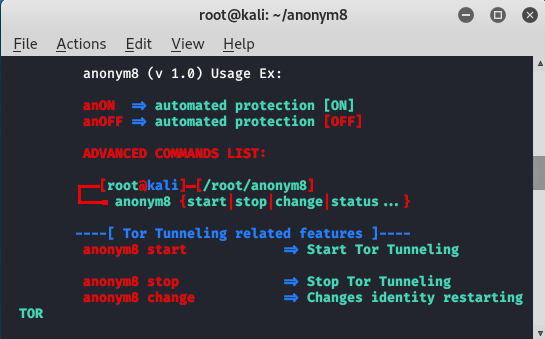
Features of Anonym8 :
- Anonym8 uses IP-tables
- Anonym8 uses tor proxy
- Anonym8 uses tor tunnel
- through Anonym8 network can redirected through IP tables.
- Anonym8 is easy to use.
- Anonym8 can change your system’s mac address.
Installation
Step 1: Open your Kali Linux. Move to your terminal and install the tool using the following command.git clone GitHub - HiroshiManRise/anonym8: Sets Transparent proxy tunnel through Tor, I2P, Privoxy, Polipo and modify DNS; Include Anonymizing Relay Monitor (arm), macchanger and wipe (Cleans ram/cache & swap-space) features, ID spoofing has never been so easy.
cd anonym8
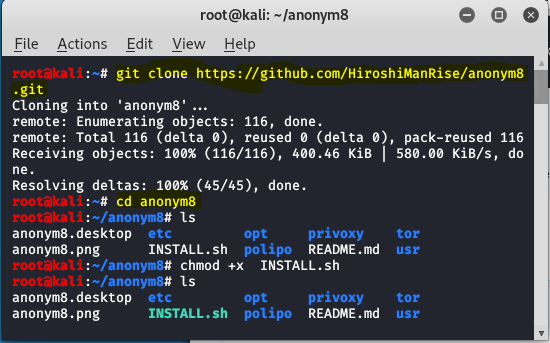
Step 2: Now you have to give permission to the tool using the following command.
chmod +x INSTALL.sh
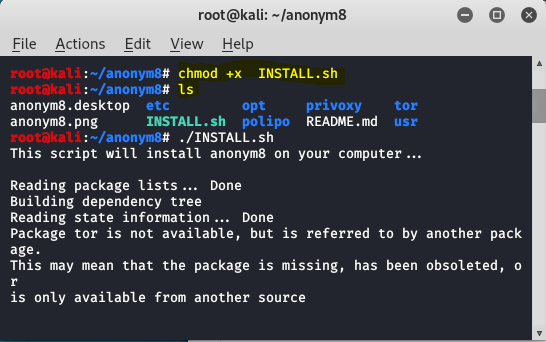
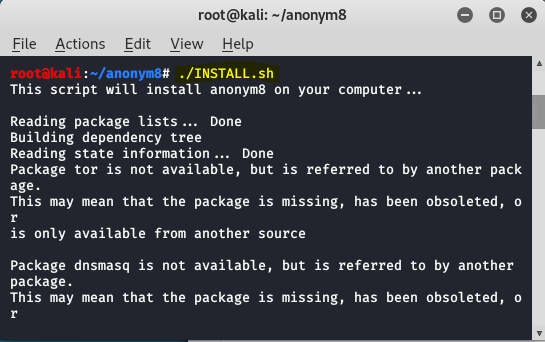
Step 3: To install the tool use the following command.
INSTALL.sh
Usage
Example 1:Now to see the status and to change the IP address use the following command.
anonym8 status_ip
Before that, first check the original IP address
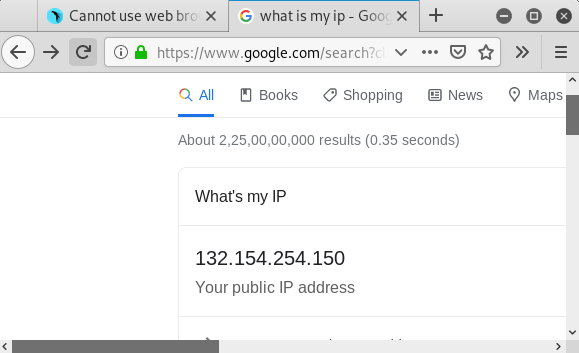
after running the command
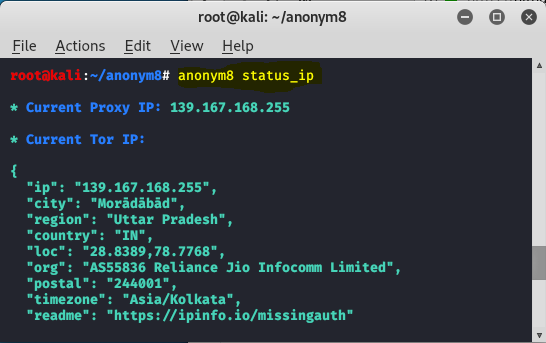
after running the tool.
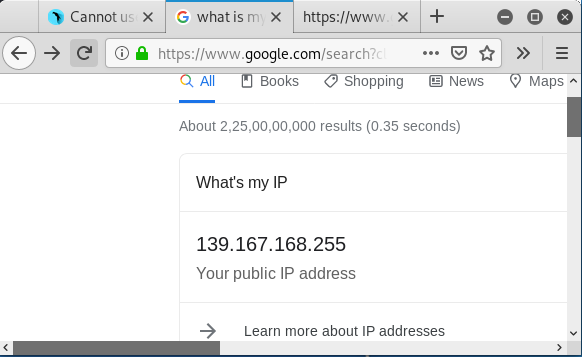
You can see that IP address has been changed. Similarly, you can change your IP address while testing any site.
Example 2:
Now to spoof the mac address, use the following command.
anonym8 start_mac
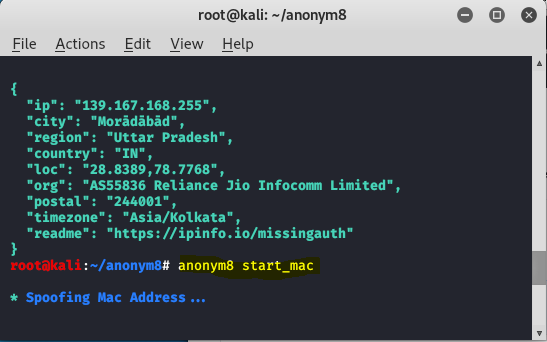
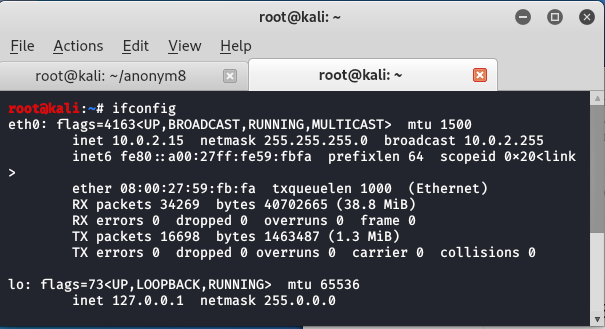
You can see that eth is changed and the flags values are different from each other.
This is how you can perform these experiments on your system. You can also spoof your mac address. The MAC address is the same as the Ethernet address on the Ethernet LAN. In telecommunication protocols, the media access control, which is the sublayer of the data-link layer, uses the MAC address.

